Qualys Vulnerability Management (VMDR)
Redefining Cyber Risk Management
Cyber risk is business risk – with risks growing faster than what traditional VM and SIEM tools can manage. Security and IT teams need a new approach to tackle cyber threats with a clear understanding of cybersecurity risk and automate workflows for rapid response.
Cyber risk is business risk – with risks growing faster than what traditional VM and SIEM tools can manage. Security and IT teams need a new approach to tackle cyber threats with a clear understanding of cybersecurity risk and automate workflows for rapid response.
Qualys VMDR
With VMDR, enterprises are empowered with visibility and insight into cyber risk exposure - making it easy to prioritize vulnerabilities, assets, or groups of assets based on business risk. Security teams can take action to mitigate risk, helping the business measure its true risk, and track risk reduction over time.
With VMDR, enterprises are empowered with visibility and insight into cyber risk exposure - making it easy to prioritize vulnerabilities, assets, or groups of assets based on business risk. Security teams can take action to mitigate risk, helping the business measure its true risk, and track risk reduction over time.
Understand and manage cybersecurity risk
Quantify risk across vulnerabilities, assets, and groups of assets to help your organization proactively mitigate risk exposure and track risk reduction over time with TruRisk™
Prevent attacks from ever happening
Leverage insights from over 180k vulnerabilities sourced from over 25+ threat sources to receive preemptive alerts on potential attacks with the Qualys Threat DB
Analyze vulnerabilities and misconfigurations with six sigma accuracy
Automatically detect vulnerabilities and critical misconfigurations per Center for Internet Security (CIS) benchmarks, by asset
Automate remediation with no-code workflows
Save valuable time by automating and orchestrating operational tasks for vulnerability management and patching with Qualys Flow
Identify all assets in your environment
Detect all IT, OT, and IoT assets for a complete, categorized inventory enriched with details such as vendor lifecycle information and much more
Quickly remediate threats at scale
Rule-based integrations with ITSM tools such as ServiceNow and JIRA automatically assign tickets and enable orchestration of remediation to reduce MTTR
Qualys Vulnerability Management (VMDR)
A single solution for cybersecurity risk, discovery, assessment, detection, and response
Qualys VMDR offers an all-inclusive risk-based vulnerability management solution to prioritize vulnerabilities and assets based on risk and business criticality. VMDR seamlessly integrates with configuration management databases (CMDB) and patch management solutions to quickly discover, prioritize, and automatically remediate vulnerabilities at scale to reduce risk. Additionally, it integrates with ITSM solutions such as ServiceNow to automate and operationalize vulnerability management end-to-end.
Get an all-Inclusive risk-based vulnerability management solution that prioritizes vulnerabilities, misconfigurations and assets based on risk, reduces risk by remediating vulnerabilities at scale, and helps organizations measure security program effectiveness by tracking risk reduction over time.
Qualys VMDR offers an all-inclusive risk-based vulnerability management solution to prioritize vulnerabilities and assets based on risk and business criticality. VMDR seamlessly integrates with configuration management databases (CMDB) and patch management solutions to quickly discover, prioritize, and automatically remediate vulnerabilities at scale to reduce risk. Additionally, it integrates with ITSM solutions such as ServiceNow to automate and operationalize vulnerability management end-to-end.
Get an all-Inclusive risk-based vulnerability management solution that prioritizes vulnerabilities, misconfigurations and assets based on risk, reduces risk by remediating vulnerabilities at scale, and helps organizations measure security program effectiveness by tracking risk reduction over time.
Qualys VMDR covers all your rapid remediation needs, leveraging risk-based VM and easy-to-use no-code workflows. VMDR is priced on a per-asset basis and does not require a software update to start. Sign up for a free trial or request a quote.
Qualys Cloud Platform, combined with its powerful lightweight Cloud Agent, Virtual Scanners, and Network Analysis (passive scanning) capabilities bring together all four key elements of an effective vulnerability management program into a single app unified by powerful out-of-the-box orchestration workflows.
Qualys VMDR enables organizations to automatically discover every asset in their environment, including unmanaged assets appearing on the network, inventory all hardware and software, and classify and tag critical assets. VMDR continuously assesses these assets for the latest vulnerabilities and applies the latest threat intel analysis to prioritize actively exploitable vulnerabilities.
Finally, VMDR automatically detects the latest superseding patch for the vulnerable asset and easily deploys it for remediation. By delivering all this in a single app workflow, VMDR automates the entire process and significantly accelerates an organization’s ability to respond to threats, thus preventing possible exploitation.
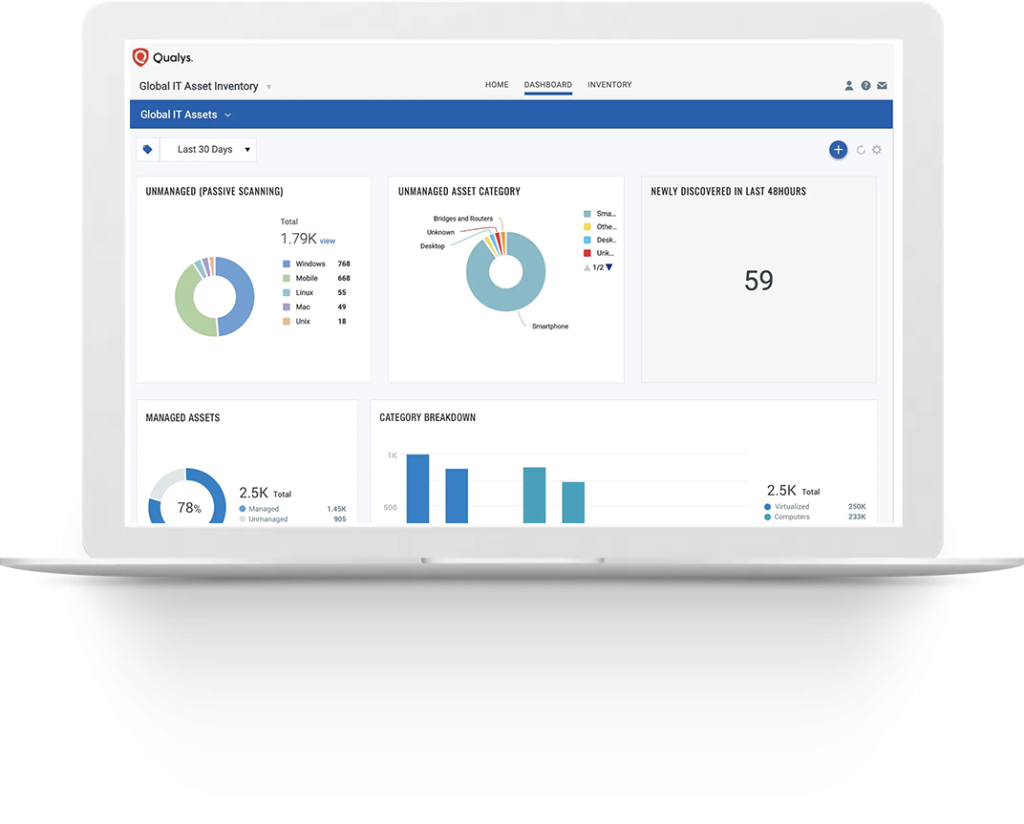
ASSET MANAGEMENT - Automated asset identification and categorization
Knowing what’s active in a global hybrid-IT environment is fundamental to security. Qualys VMDR enables customers to automatically discover and categorize known and unknown assets, continuously identify unmanaged assets, and create automated workflows to manage them effectively.
After the data is collected, customers can instantly query assets and any attributes to get deep visibility into hardware, system configuration, applications, services, network information, and more.
Knowing what’s active in a global hybrid-IT environment is fundamental to security. Qualys VMDR enables customers to automatically discover and categorize known and unknown assets, continuously identify unmanaged assets, and create automated workflows to manage them effectively.
After the data is collected, customers can instantly query assets and any attributes to get deep visibility into hardware, system configuration, applications, services, network information, and more.
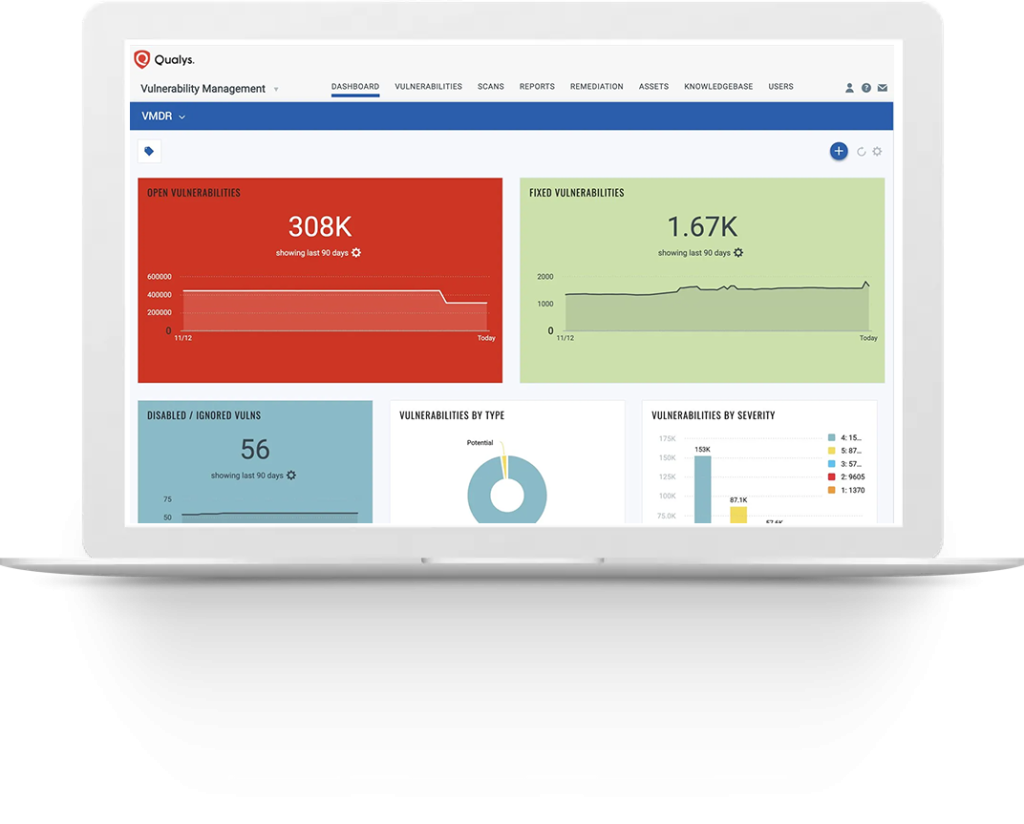
VULNERABILITY MANAGEMENT - Real-time vulnerability and misconfiguration detection
Qualys VMDR enables customers to automatically detect vulnerabilities and critical misconfigurations per CIS benchmarks, broken out by asset. Misconfigurations lead to breaches and compliance failures, creating vulnerabilities on assets without common vulnerabilities and exposures (CVEs). VMDR continuously identifies critical vulnerabilities and misconfigurations on the industry’s widest range of devices, including mobile devices, operating systems and applications.
THREAT PRIORITIZATION
Automated vulnerability remediation prioritization with context
Qualys VMDR uses real-time threat intelligence, advanced correlation and powerful machine learning models to automatically prioritize the riskiest vulnerabilities on your most critical assets – reducing potentially thousands of discovered vulnerabilities, to the few hundred that matter. Indicators such as Exploitable, Actively Attacked, and High Lateral Movement bubble up current vulnerabilities that are at risk while machine learning models highlight vulnerabilities most likely to become severe threats, providing multiple levels of prioritization.
Further prioritize remediation by assigning a business impact to each asset, like devices that contain sensitive data, mission-critical applications, public-facing, accessible over the Internet, etc.
Qualys VMDR uses real-time threat intelligence, advanced correlation and powerful machine learning models to automatically prioritize the riskiest vulnerabilities on your most critical assets – reducing potentially thousands of discovered vulnerabilities, to the few hundred that matter. Indicators such as Exploitable, Actively Attacked, and High Lateral Movement bubble up current vulnerabilities that are at risk while machine learning models highlight vulnerabilities most likely to become severe threats, providing multiple levels of prioritization.
Further prioritize remediation by assigning a business impact to each asset, like devices that contain sensitive data, mission-critical applications, public-facing, accessible over the Internet, etc.

